SMTP: The Key Player in Email Delivery and Communication
Installation and configuration of a SMTP Mail Server on a Unix based machine.
Operating System: Raspbian GNU/Linux 10 (buster).
Postfix SMTP Version: 3.4.14.
Dovecot IMAP Version: 2.3.4.1.
ClamAV Antivirus Version: 0.103.2.
Overview
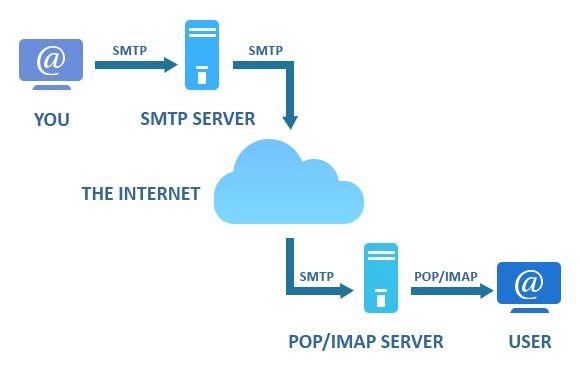
An email service provides a means to send electronic mail between nodes within a computer network. It operates through the Simple Mail Transfer Protocol (SMTP), which relies on the TCP/IP suite. It follows a client-server communication model. The client establishes a TCP communication channel on port 25 (port 587 for Secure SMTP) with the server and communicates the email recipient to it. Once the server accepts the destination, the client can send the content of the email. The initial mail server to which the client connects is not always the final network node for email delivery. SMTP is designed to forward email to other mail servers until the recipient node is reached. Intermediate servers are known as Mail Transfer Agents (MTA). Once the email reaches the destination node, the final server stores the entire email in its file system.
The data format of an email is defined by RFC 5322, 2045, and 2049. The main components of an email are headers and the body.
HEADER: The header consists of a series of lines, each composed of a type and a value, including:
- From: sender's address
- To: recipient mailbox (can have multiple recipients)
- Date: sending date
- Subject: message subject
- Cc: copy recipients
- Reply-To: reply address
- Message-Id: unique message identifier
BODY: The body of the message is the text of the email in ASCII format.
An email address follows the form "local-part@domain" (without quotation marks) and it consists of two fields separated by @: the username of the recipient and the domain. For example, the email address local-part@domain has local-part as the username and domain as the domain. It's important to note that an email address can have aliases, representing the same address.
The main components involved are:
- User Agent (UA), which interfaces with the user.
- Mail Transfer Agent (MTA), the mail servers. An email starts from the sender's UA and reaches the recipient's UA through a network of MTAs. SMTP is used for mail delivery to the recipient's mailbox (push model).
- MTAs use SMTP.
- The sending UA uses SMTP.
Once the email arrives at the destination and is stored in the recipient's file system, other specific protocols like POP3 or IMAP (or their secure versions, POP3s and IMAPS) are used for email retrieval. These protocols follow the pull model, meaning they transfer email from the user's mailbox to the UA for viewing.
SMTP commands are ASCII strings, including HELO, MAIL, RCPT, DATA, and QUIT. Responses are encoded with three digits and descriptive text, with the first digit indicating interactions (1xx accepted, 2xx positive response, 3xx intermediate positive response, 4xx transient negative response, 5xx permanent negative response). The second digit specifies the response type, and the third digit refines the message further.
Section 2.1: Installation
Our first step is to install the Postfix Server on our Unix-based system. To install Postfix, follow these steps:
- Open a terminal window on your Unix-based system.
- Update the package list by running:
sudo apt update
- Install Postfix with the following command:
sudo apt install postfix
- Once the installation is complete, start the Postfix service and enable it to start on boot with these commands:
sudo systemctl start postfix
sudo systemctl enable postfix
Section 2.2: Configuration
Postfix uses two configuration files, namely:
/etc/postfix/main.cf
/etc/postfix/master.cf
In the main.cf file, you should make changes to the following fields:
myhostname = smtp.gruppo9.labreti.it
mydomain = gruppo9.labreti.it
myorigin = $mydomain
The myhostname variable indicates the Fully Qualified Domain Name (FQDN) of the mail server, which should be consistent with your DNS configuration.
The mydomain variable indicates the email domain.
The myorigin variable specifies the domain used in the emails sent by the server.
mydestination = gruppo9.labreti.it
This field specifies that email with the domain "gruppo9.labreti.it" should not be forwarded further but instead saved in the file system.
home_mailbox = Maildir/
This field indicates where to save the emails within the file system. Specifically, within each user's home directory, an automatically created directory called "Maildir" will contain subdirectories named new, cur, and tmp, where emails destined for this server are stored.
Section 2.3: BIND9 Configuration
To enable name resolution for the newly installed mail server, you need to make some changes to the existing zone in the name server on your network. Specifically, you should add a new CNAME record that allows the resolution of "smtp.gruppo9.labreti.it" to an IP address and a new MX record that indicates the existence of the mail server smtp.gruppo9.labreti.it for the domain gruppo9.labreti.it.
Here is how you can modify the db.gruppo9.labreti.it file:
$TTL 604800
$ORIGIN gruppo9.labreti.it.
@ IN SOA ns.gruppo9.labreti.it. admin.gruppo9.labreti.it. (
1 ; Serial
604800 ; Refresh
86400 ; Retry
2419200 ; Expire
604800 ) ; Negative Cache TTL
;
@ IN NS ns.gruppo9.labreti.it.
@ IN A 192.168.9.1
IN AAAA 2009::1
progetto IN A 192.168.9.2
IN AAAA 2009::2
www IN A 192.168.9.3
IN AAAA 2009::3
ftp IN A 192.168.9.4
IN AAAA 2009::4
host1 IN A 192.168.9.5
IN AAAA 2009::5
host2 IN A 192.168.9.6
IN AAAA 2009::6
@ IN MX 10 smtp.gruppo9.labreti.it.
smtp IN CNAME progetto.gruppo9.labreti.it.
imap IN CNAME progetto.gruppo9.labreti.it.
In the above file:
- The MX record
@ IN MX 10 smtp.gruppo9.labreti.it.specifies that mail for the domain "gruppo9.labreti.it" should be directed to "smtp.gruppo9.labreti.it." - The CNAME records
smtp IN CNAME progetto.gruppo9.labreti.it.andimap IN CNAME progetto.gruppo9.labreti.it.create aliases for "smtp.gruppo9.labreti.it" and "imap.gruppo9.labreti.it" to point to "progetto.gruppo9.labreti.it."
Make sure to adjust the values to match your specific configuration. After making these changes, don't forget to reload or restart your DNS server for the new settings to take effect.
Section 3: SMTP with TLS
SMTP was not designed to send encrypted data; instead, SSL/TLS is used to encrypt the data being sent as a wrapper protocol around SMTP. To enable the use of the SSL/TLS protocol, you can use the following subcommands and steps with Postfix:
To enable the use of SSL/TLS:
postfix tls enable-server
This command enables the TLS protocol for the server.
To automatically create a new private key and a self-signed certificate for the email server:
postfix tls new-server-key [hostname]
Replace [hostname] with the fully qualified domain name (FQDN) of your email server, in this example, "smtp.gruppo9.labreti.it."
Deploy the certificate and key generated in step 2:
postfix tls deploy-server-cert /etc/postfix/cert-20210417-201237.pem /etc/postfix/key-20210417-201237.pem
This command updates the Postfix configuration to use the newly generated certificate and key. Note that the certificate and key filenames may vary.
Reload the Postfix daemon to apply the changes:
postfix reload
This command tells the Postfix daemon to reload its configuration with the TLS settings.
To activate port 587 for secure email submission, make the following modifications to the master.cf file:
In the master.cf file, locate the following lines and ensure they are configured as follows:
submission inet n - y -o syslog_name=postfix/submission -o smtpd_tls_security_level=encrypt -o smtpd_sasl_auth_enable=yes
smtps inet n - y -o syslog_name=postfix/smtps -o smtpd_tls_wrappermode=yes -o smtpd_sasl_auth_enable=yes
These configurations specify settings for secure email submission and SMTPS (SMTP over SSL/TLS).
Make sure to save your master.cf file after making these changes. With these configurations, you should have SSL/TLS encryption enabled for your Postfix email server, making email communication more secure.
Section 4: Configuration Test
Once you have configured Postfix to work both in plaintext and encrypted mode using SSL/TLS, you can test the server's functionality using the telnet and openssl commands. Here's how you can perform a test on the smtp.gruppo9.labreti.it server:
Using Telnet on Port 25:
Open a connection to port 25 with the SMTP server using telnet:
telnet smtp.gruppo9.labreti.it 25
Once the connection is open, you should follow this series of commands. Each command will correspond to a response from the server:
ehlo smtp.gruppo9.labreti.it
mail from: <pi@gruppo9.labreti.it>
rcpt to: <pi@gruppo9.labreti.it>
data
This is a test.
. (This period indicates the end of the message)
quit
You will receive responses from the server after each command, confirming its status. After the quit command, you should see:
221 2.0.0 Bye
This indicates that the connection has been closed.
After completing these steps, you should find a new file in the user's pi directory representing the email that was just sent. It will be located at /home/pi/Maildir/new.
Using OpenSSL on Port 587:
To test port 587 with the openssl command, you can use the following:
openssl s_client -starttls smtp -connect smtp.gruppo9.labreti.it:587
This command establishes an SSL/TLS connection to the SMTP server on port 587 and allows you to interact with it securely.
By following these procedures, you can test the functionality of your Postfix email server over both plaintext (port 25) and encrypted (port 587) connections.
Section 5: IMAP Overview
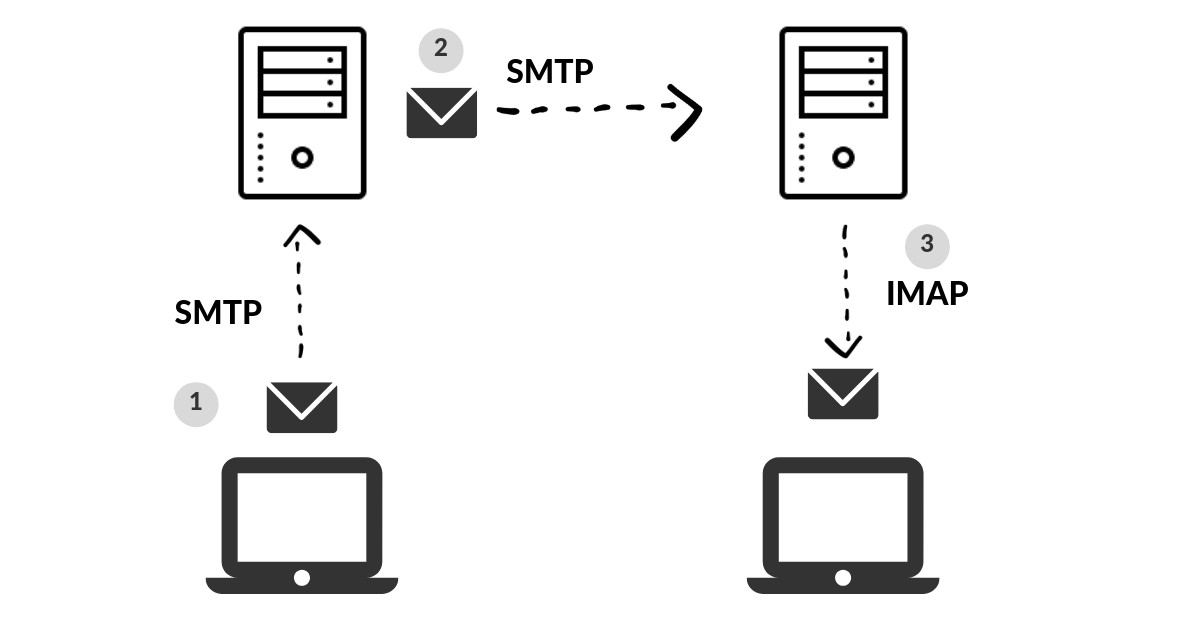
SMTP allows you to send email within a network of nodes, but it doesn't provide the capability to read emails. To address this need, a second protocol called IMAP (Internet Message Access Protocol) was developed, which works in conjunction with SMTP. An IMAP server is also known as an MDA (Mail Delivery Agent) because it allows the delivery of emails to the recipient's user account. IMAP is used to connect to the server where the email is stored within its file system and copy it to the client machine for reading.
It's essential to note that the email is copied, not moved, so that multiple copies can be downloaded to various devices. In this case, the communication model used is client-server (pull) over TCP/IP. The ports used are 143 for unencrypted communication and 993 for encrypted communication.
Dovecot, in addition to offering IMAP functionality, provides features such as creating various email folders like Inbox, Trash, Drafts, Sent, etc.
To use the IMAP protocol, you must first complete an authentication phase. Before using it, you need a username and password for authentication.
Section 5.1: Installation
The command to install the Dovecot IMAP server is:
sudo apt install dovecot-imapd
Section 5.2: Configuration
Dovecot's configuration is based on the /etc/dovecot/dovecot.conf file, which includes all the files inside the /etc/dovecot/conf.d/ directory through a directive.
For configuring Dovecot to work with Postfix, you can make changes to the configuration files as follows:
In the /etc/dovecot/conf.d/10-master.conf file:
service auth {
unix_listener /var/spool/postfix/private/auth {
mode = 0660
user = postfix
group = postfix
}
}
This configuration specifies that Dovecot should communicate with Postfix via a Unix socket using SASL (Simple Authentication and Security Layer).
In the same /etc/dovecot/conf.d/10-master.conf file:
mail_location = maildir:~/Maildir
This line specifies that the access and storage system to use is Maildir, which is the same as what Postfix is using.
Postfix also needs to be configured to work with Dovecot, specifically allowing authentication using SASL. In the /etc/postfix/main.cf file:
smtpd_sasl_type = dovecot
smtpd_sasl_path = private/auth
smtpd_sasl_auth_enable = yes
smtpd_recipient_restrictions = permit_sasl_authenticated, permit_mynetworks, reject_unauth_destination
These settings enable SASL authentication with Dovecot for Postfix.
After making these configurations, you may need to restart both Dovecot and Postfix for the changes to take effect.
Section 5.3: IMAP with TLS
To enhance the security of IMAP (Internet Message Access Protocol) in Dovecot, you should enable TLS/SSL and make the following changes to the configuration files:
Enable TLS/SSL in Dovecot:
In the /etc/dovecot/conf.d/10-ssl.conf file, set the ssl parameter to "yes":
ssl = yes
Additionally, specify the paths to the SSL certificate and key files:
ssl_cert = </etc/dovecot/private/dovecot.crt
ssl_key = </etc/dovecot/private/dovecot.key
Ensure you have SSL certificate and key files available. You can create them using the following OpenSSL commands:
# Generate a private key
openssl genrsa -aes256 -out /etc/dovecot/private/dovecot.key 2048
# Create a certificate signing request (CSR)
openssl req -new -key /etc/dovecot/private/dovecot.key -out /etc/dovecot/private/dovecot.csr
# Generate a self-signed certificate (or obtain a signed one from a certificate authority)
openssl req -new -x509 -days 365 -signkey /etc/dovecot/private/dovecot.key -in /etc/dovecot/private/dovecot.csr -out /etc/dovecot/private/dovecot.crt
Restrict Plaintext Authentication:
In the /etc/dovecot/conf.d/10-auth.conf file, disable plaintext authentication by setting the disable_plaintext_auth parameter to "yes":
disable_plaintext_auth = yes
This configuration ensures that login requests are only accepted if the channel between the client and server is encrypted with TLS/SSL.
After making these changes, you'll need to restart the Dovecot service for the new configurations to take effect:
sudo systemctl restart dovecot
With these settings in place, Dovecot will enforce TLS/SSL encryption for secure communication between IMAP clients and the server, enhancing the security of your email communication.
Section 5.4: Configuration Test
Once you have completed the configuration, you can perform some checks to ensure the correct functioning of the IMAP server. You can use the telnet and openssl commands as demonstrated previously.
For example, to check IMAP functionality over a plaintext connection on port 143, you can use the following telnet command:
telnet imap.gruppo9.labreti.it 143
If the IMAP server is correctly configured and operational, you should receive a response similar to the following:
* OK [CAPABILITY IMAP4rev1 SASL-IR LOGIN-REFERRALS ID ENABLE IDLE LITERAL+ STARTTLS AUTH=PLAIN] Dovecot (Raspbian) ready.
You can then proceed to log in with your system credentials and select the inbox, as you demonstrated in your example.
To check the encrypted communication over port 993, you can use the openssl command as follows:
openssl s_client -connect imap.gruppo9.labreti.it:993
This command will establish an SSL/TLS-encrypted connection to the IMAP server on port 993. If the encryption is correctly configured, you should see the SSL/TLS negotiation and a successful connection.
These tests help verify the availability of the IMAP service on your local network and ensure that you can log in with your operating system credentials and access your inbox. Additionally, the encrypted connection test checks the security of the IMAP server's SSL/TLS configuration.
Section 6: ClamAV Overview
ClamAV is a toolkit designed to detect the presence of malicious code, often referred to as viruses. It is commonly used in conjunction with Postfix to scan email messages for the presence of viruses.
ClamAV operates as a filter that takes the input from the SMTP server and analyzes it to identify malicious code. Email messages that pass this scan are forwarded to the SMTP server for delivery, while messages containing malicious code are typically quarantined or deleted to prevent them from reaching the recipient's inbox.
The integration of ClamAV into a mail server setup is an essential security measure, as it helps protect against email-borne threats, including viruses and malware. By scanning incoming and outgoing email traffic, ClamAV helps ensure that only clean and safe messages are delivered to users' mailboxes.
To effectively set up ClamAV with Postfix or another mail server, you would typically need to configure the server to use ClamAV as an antivirus scanner. This configuration ensures that all email messages passing through the server are checked for malware. Additionally, regular updates to ClamAV's virus signature database are crucial to maintaining the effectiveness of the antivirus scanner, as new threats are continuously emerging.
Overall, ClamAV plays a crucial role in enhancing the security of email communication by identifying and mitigating email-borne threats, ultimately safeguarding the integrity of email systems and protecting users from malicious content.
Section 6.1: Installation
apt-get install clamav clamsmtp clamav-freshclam
Section 6.2: Configuration
In the configuration you provided, you are setting up Postfix to work with an email content filtering service, which appears to be named "scan." This setup allows you to send all incoming email through this content filter for scanning and processing. Here's a breakdown of the configuration changes made to /etc/postfix/main.cf and /etc/postfix/master.cf:
- /etc/postfix/main.cf:
...
content_filter = scan:127.0.0.1:10026
receive_override_options = no_address_mappings
...
In the main configuration file, you've added the content_filter parameter, which specifies that all incoming email should be sent to the "scan" service running on localhost (127.0.0.1) at port 10026. The receive_override_options parameter is set to no_address_mappings, indicating that address mappings should not be performed.
- /etc/postfix/master.cf:
...
scan unix - - n - 16 smtp
-o smtp_send_xforward_command=yes
127.0.0.1:10025 inet n - n - 16 smtpd
-o content_filter=
-o receive_override_options=no_unknown_recipient_checks,no_header_body_checks
-o smtpd_helo_restrictions=
-o smtpd_client_restrictions=
-o smtpd_sender_restrictions=
-o smtpd_recipient_restrictions=permit_mynetworks,reject
-o mynetworks_style=host
-o smtpd_authorized_xforward_hosts=127.0.0.0/8
In the master configuration file, you've defined two services:
The "scan" service, which is set up to process incoming email. It's a Unix-based service with various options. The -o smtp_send_xforward_command=yes option enables the XFORWARD command for forwarding information about the original client.
The 127.0.0.1:10025 service, which listens on localhost (127.0.0.1) at port 10025. This service receives email from the "scan" service. Several options are set to configure how email is handled. Notably, content_filter is empty (-o content_filter=), indicating that filtered email is passed through this service. Various smtpd_* options are used to control access, and mynetworks_style is set to "host" to permit network access.
These configurations are typically used when integrating an email content filtering system (e.g., an antivirus scanner like ClamAV) with Postfix. The email content filtering service can scan emails for malware or perform other checks before allowing them to be delivered.
Section 7: Conclusion
Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur. Excepteur sint occaecat cupidatat non proident, sunt in culpa qui officia deserunt mollit anim id est laborum.